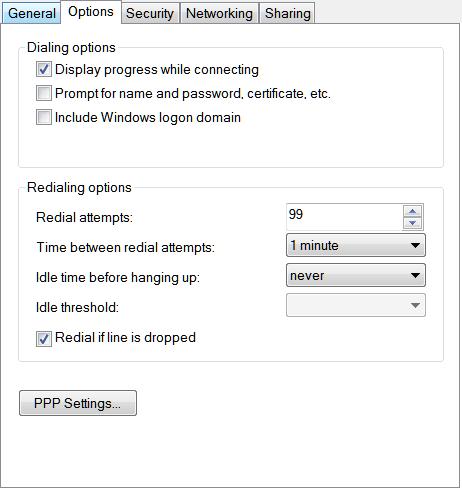
I was surprised, not much, however, when I found that in Windows 8 and Windows Server 2008 or higher Microsoft had slightly “refined” the VPN connection settings. To be more precise, removed a number of settings in the Options tab. Here is what it looked like in Windows 7:
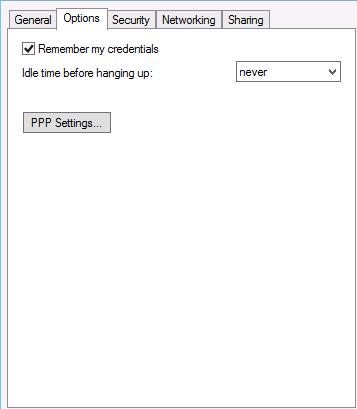
Now(Windows 8, Windows 10) almost everything has been removed:
A natural question has arised — how to configure automatic reconnection and the number of attempts to establish the connection if it is interrupted?
There are several ways to do it. Let’s start with the beginning, according to the level of difficulty.
Method 1 — Using Notepad
You have to set the parameters manually. To do it, go to the folder
C:\Users\[USER]\AppData\Roaming\Microsoft\Network\Connections\Pbk\
There, find a file (it is likely to be only one) with the name rasphone.pbk. It is a usual text file, which contains the VPN connection settings
You can open this file using notepad.exe
Usually you have to find a section containing your VPN, e. g., like this [PPTP-VPN]
Find the lines in it. If you haven’t made any changes, they look like this:
RedialAttempts=3
RedialSeconds=60
IdleDisconnectSeconds=0
RedialOnLinkFailure=1
So Microsoft has decided it for you again.
But now you know where to find and change the necessary parameters.
- RedialAttempts=3 – the number of redial attempts (99 maximum)
- RedialSeconds=60 – the number of seconds between the redial attempts
- IdleDisconnectSeconds=0 — the waiting time before it becomes clear that there is a disconnection (0 – don’t wait)
- RedialOnLinkFailure=1 — Redial if connection fails? 1 – yes, 0 – no
To apply the parameters, you have to restart your VPN connection, as earlier.
And then believe that Microsoft will do everything for you
Method 2 — Configuration of a Simple Task
Create a task in Task Scheduler, which will run a BAT file containing the VPN connection string and configure this task so that it runs, say, every 5 minutes.
I should remind that the command string to establish a VPN connection looks like this:
C:\windows\system32\rasdial.EXE entryname [username [password|*]] [/DOMAIN:domain]
There are other parameters, but if it is interesting to you find them yourself.
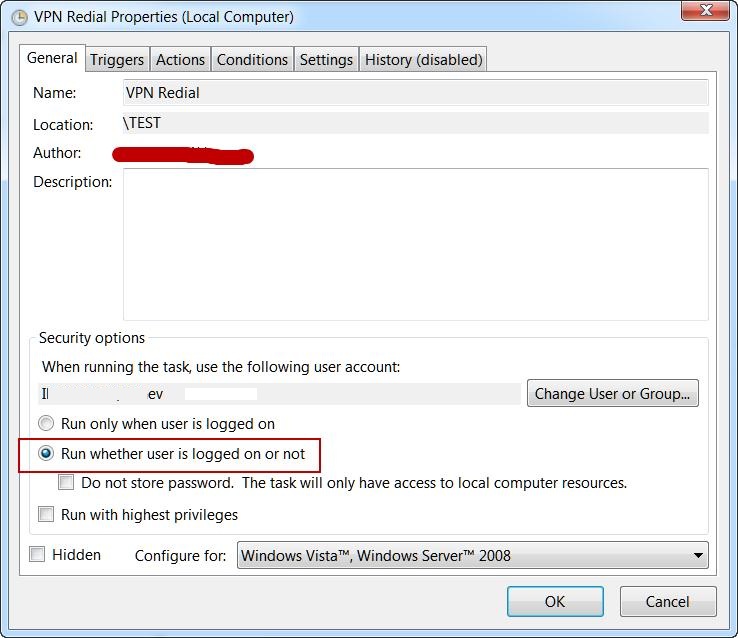
Don’t forget to check “Run whether user is logged on or not” in the task settings
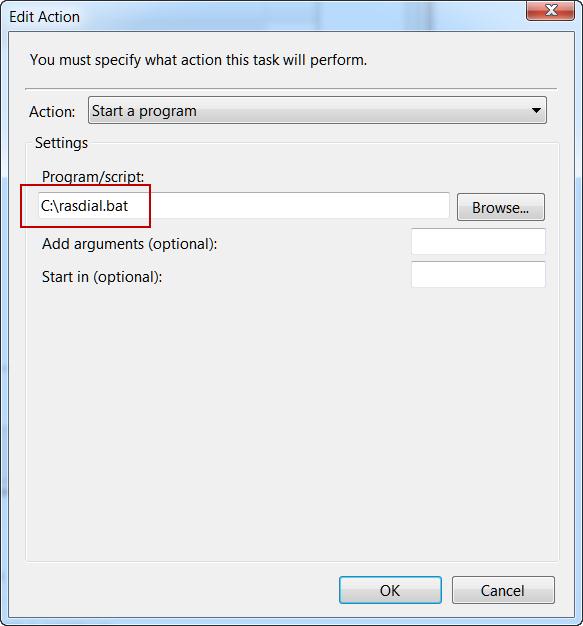
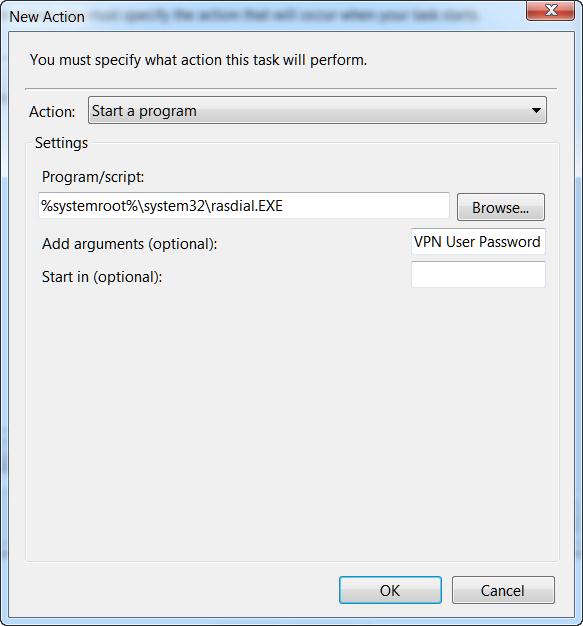
Specify the executable file, for example:
Or let rasdial.exe start (VPN User Password is the name of your VPN connection, user_name and password)
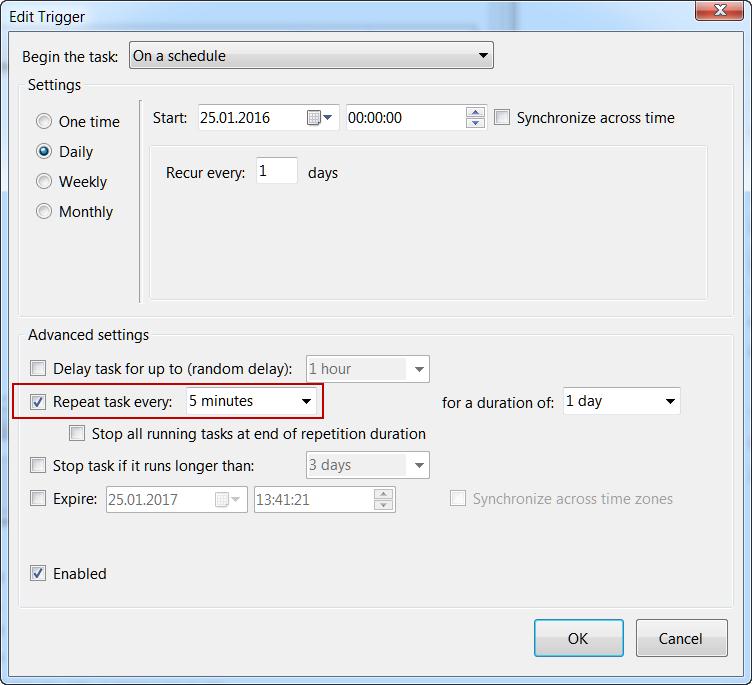
Start it every 5 minutes every day.
Method 3 — Configure a Tricky Task
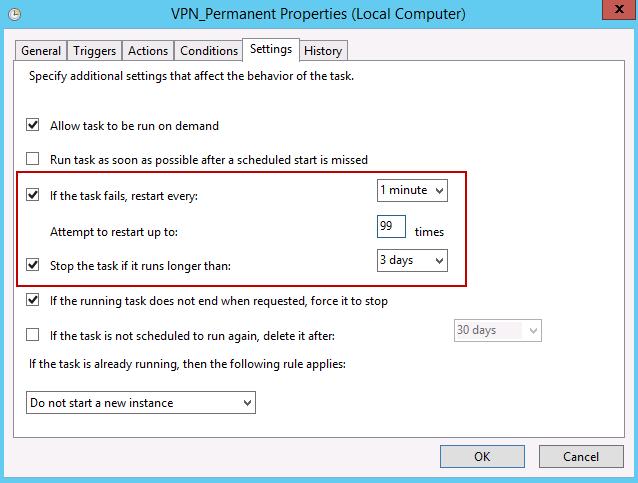
- Create a task in Task Scheduler
- Set two triggers in the task. The first one will use an XML query (like it has been described in the article “How to Start a Scheduler Task After the Previous Task“)
<QueryList>
<Query Id="0" Path="Application">
<Select Path="Application">*[System[Provider[@Name='RasClient'] and (EventID=20226)]] and *[EventData[Data[4]='829' or '629']]</Select>
</Query>
</QueryList>
The second trigger is based on tracking of the event in the Event Log:
- Log name: Microsoft-Windows-NetworkProfile/Operational
- Source: NetworkProfile
- Event ID: 10000
- Select rasdial.exe with the parameters vpn-name username password as a program to be started
- Also, in the Conditions tab, you can check the following parameters:
That’s all.
1 comment
Thanks SO much for this guide. After upgrading from W7 to W10, this was bugging the hell out of me. Thank to this, I was even able to create a “VPN Alternate” task, which looks for an 809 Error Code (ERROR_VPN_TIMEOUT aka VPN server unresponsive) in the Event Log and then dial an alternate VPN server. I simply created the same Tricky Task as above, but edited this line of the XML query:
*[EventData[Data[4]=’829′ or ‘629’]]
…to this:
*[EventData[Data[4]=’809′]]