The Just Enough Administration (JEA) feature is available starting from PowerShell version 5.0 and allows you to delegate administrative privileges to anything you can manage with PowerShell. The main purpose of PowerShell JEA is to limit privileges. JEA allows you to grant non-admin users permissions to perform specific administrative tasks without giving them server or service administrator rights (AD, Exchange, SharePoint, etc.). Using JEA, you can set which users can run specific cmdlets, functions or PowerShell scripts with admin privileges and log all actions (similar to PowerShell command history).
An administrator creates a PowerShell session configuration file on a server containing commands a user can run. Based on the files, a JEA endpoint is created a user can connect to and execute any of the commands or programs available to him.
Here we will show an example how to grant non-admin users permission to reboot a domain controller, and restart DNS and ADDS services on it.
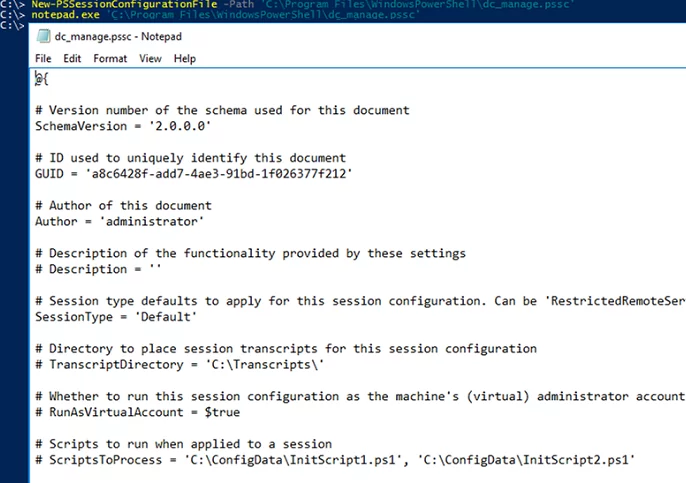
First of all, create a configuration file of a PowerShell session (*.pssc). To do it, run this command on your domain controller:
New-PSSessionConfigurationFile -Path 'C:\Program Files\WindowsPowerShell\dc_manage.pssc'
Open the PSSC file using the Notepad.
The PSSC file sets who may connect to this JEA endpoint and under what account the commands in the JEA session will run.
Modify the following values:
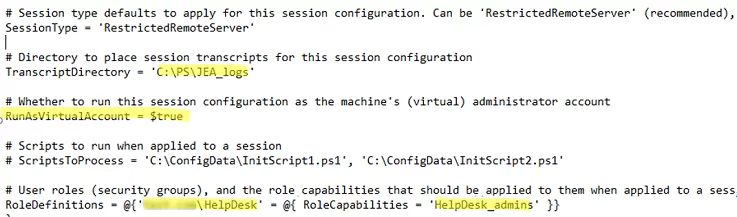
- SessionType from Default to RestrictedRemoteServer. This mode allows to use the following PowerShell cmdlets: Clear-Host, Exit-PSSession, Get-Command, Get-FormatData, Get-Help, Measure-Object, Out-Default or Select-Objectl
- Specify a folder (create it) in the TranscriptDirectory parameter. Here you will log all JEA user actions:
TranscriptDirectory = C:\PS\JEA_logs - The RunAsVirtualAccount option allows to run commands under a virtual administrator account (member of the local Administrator or Domain Administrator group):
RunAsVirtualAccount = $true
GroupManagedServiceAccount = 'woshub\gMSAJEAUser'In the RoleDefinitions directive, specify the AD security group allowed to connect to the PowerShell session and the name of the JEA role (it must match the PSRC file name we are going to create later).
For example:
RoleDefinitions = @{‘woshub.com\HelpDesk' = @{ RoleCapabilities = 'HelpDesk_admins' }}Save the session configuration file.
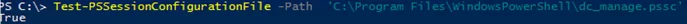
Test-PSSessionConfigurationFile -Path 'C:\Program Files\WindowsPowerShell\dc_manage.pssc'
Create a new directory to keep the JEA configuration file, for example:
New-Item -Path 'C:\Program Files\WindowsPowerShell\Modules\JEA\RoleCapabilities ' -ItemType Directory
Then create a configuration PSRC file with the role description (use the file name from the PSSC configuration above).
New-PSRoleCapabilityFile -Path 'C:\Program Files\WindowsPowerShell\Modules\JEA\RoleCapabilities\HelpDesk_admins.psrc'
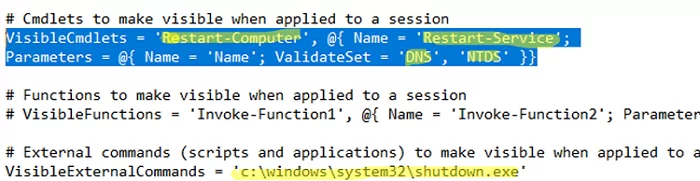
The PSRC file specifies what is allowed to do in the current JEA session. In the VisibleCmdlets directive, you may specify the cmdlets (and their valid parameters) allowed to be used for a given user group.
In the VisibleExternalCommands option, you can specify external commands and EXE files allowed to run.
For example, the following configuration allows HelpDesk users to restart the domain controller using the shutdown command or the Restart-Computer cmdlet, as well as restart DNSServer and Active Directory Domain Services using the Restart-Service cmdlet.
VisibleCmdlets = 'Restart-Computer', @{ Name = 'Restart-Service'; Parameters = @{ Name = 'Name'; ValidateSet = 'DNS', 'NTDS' }}
VisibleExternalCommands = 'c:\windows\system32\shutdown.exe'Save your PSRC file.
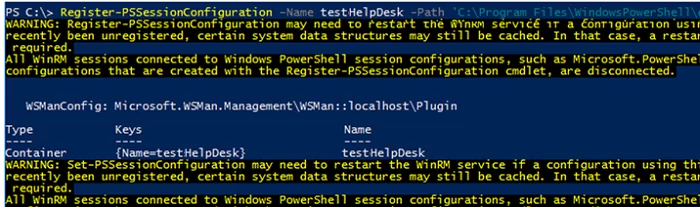
Then register a new PSSession configuration for your PSSC file:
Register-PSSessionConfiguration –Name testHelpDesk -Path 'C:\Program Files\WindowsPowerShell\dc_manage.pssc'
and restart WinRM:
Restart-Service WinRM
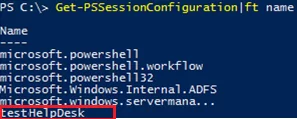
Get-PSSessionConfiguration|ft name
Let’s see how our new Just-Enough-Administration (JEA) configuration works. You can connect to the created JEA endpoint under a user account from the security group specified in the configuration file. Connect to the domain controller using PowerShell Remoting (you must specify the JEA endpoint name):
Enter-PSSession -ComputerName dc01 -ConfigurationName testHelpDesk
View the list of available cmdlets in your PowerShell session:
Get-Command
As you can see, a small number of commands is available, including Restart-Service and Restart-Computer. A user can only do what he is allowed to do.
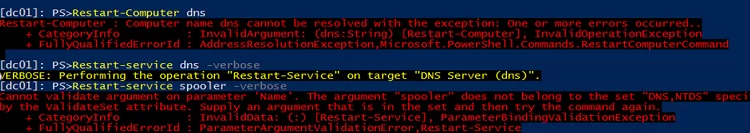
Try to restart the DNS service:
Restart-Service dns
The service has been restarted successfully (the command is run as a privileged user with the domain admin permissions).
If you try to restart any other service that is not described in the JEA configuration file, the following error message appears:
Cannot validate argument on parameter 'Name'. The argument "spooler" does not belong to the set "DNS,NTDS" specifiedby the ValidateSet attribute. Supply an argument that is in the set and then try the command again. + CategoryInfo : InvalidData: (:) [Restart-Service], ParameterBindingValidationException
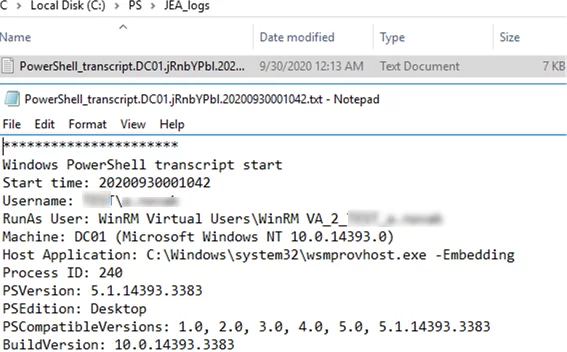
The history of all user actions in the JEA PowerShell session is logged to the files in C:\PS\JEA_logs.
So, JEA allows you to granularly grant users access to run specific PowerShell cmdlets, scripts or programs as an administrator.
2 comments
Instead Restart-Computer dns, should be Restart-Service dns
🙂 thks