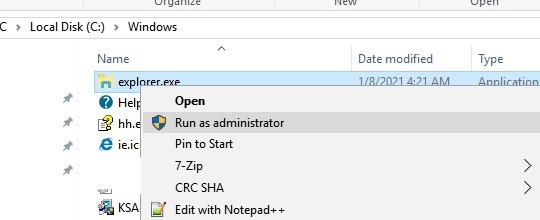
File Explorer always starts in Windows with least privileges. Even if you click on the executable file C:\Windows\explorer.exe and try to start it in the “Run as administrator” mode, the privilege elevation won’t occur. In this article we’ll look at a simple trick to run File Explorer with elevated permissions (as administrator).
You Don’t Have Permission to Access Folder, Click Continue to Permanently Get Access
When working with Windows File Explorer under an account that is added to the local administrators group (or even under the built-in Windows administrator), you often have to open system folders, user profiles or edit protected system files. When trying to open such directory/file in Windows Explorer in the current context, the UAC warning appears prompting to grant access and elevate privileges.
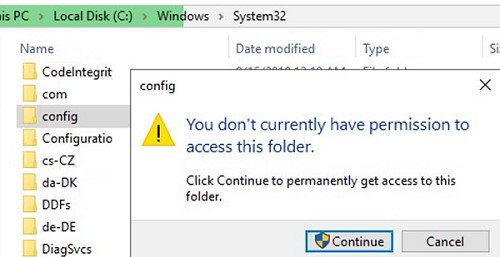
What it looks like: let’s try to open a system folder C:\Windows\System32\Config in File Explorer. User Account Control window appears to warn that you don’t currently have permission to access this folder:
You don’t currently have permission to access this folder. Click Continue to permanently get access to this folder.
But you can get the access through the UAC privilege elevation by clicking Continue.
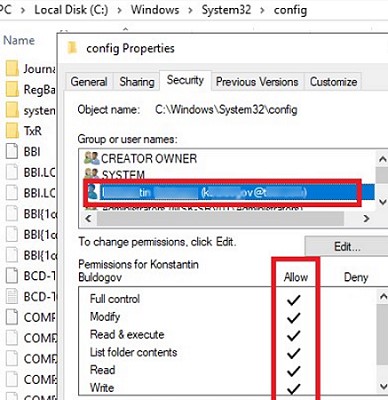
When you click Continue, UAC temporarily elevates the privileges of your explorer.exe process and grants NTFS full control permissions to your account.
Known issues:
It’s ok, but if you do , your account will be explicitly added to the folder NTFS permissions. But all you want to do is to view the contents of the folder, and not to change its ACL! What if there are multiple administrators on the server? Then each of them will change the directory ACL when accessing the folder.
After the permissions have been changed, all programs running under your user account have Full Control rights on this folder (even if the program isn’t elevated) and even after your account is removed from the local Administrators group.
\\mun-fs01\docs\) instead of locally. In this case, you don’t need to elevate privileges when accessing the directory, and hence there are no changes to NTFS ACLs.Naturally, when you often work with system files or user folders, this pop-up UAC notification becomes annoying. Since I don’t want to disable UAC, I had find the way to start the Exploler.exe elevated.
How to Run File Explorer as Administrator on Windows 10 and Windows Server?
The Windows Explorer process starts when a user logs on with the standard user access token. You cannot elevate the Explorer.exe process in the standard way. Also you won’t be able to start the second explorer process in the “Run as admin” mode (this is blocked by the CreateExplorerShellUnelevatedTask task). Windows File Explorer doesn’t support running multiple instances of the explorer.exe process in different security contexts in an interactive user session. Therefore, you first need to end the current explorer.exe process in your user session.
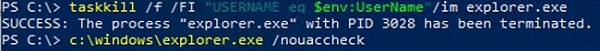
You can kill the explorer.exe process from Task Manager or with the following command in the PowerShell console (be sure to run powershell.exe as an administrator):
taskkill /f /FI "USERNAME eq $env:UserName"/im explorer.exe
SUCCESS: The process "explorer.exe" with PID 3208 has been terminated.
In order to run the explorer.exe process as administrator, use the command:
c:\windows\explorer.exe /nouaccheck
These commands will terminate the explorer.exe process for the current user and start a new one, which will inherit the elevated access token that powershell.exe is run with.
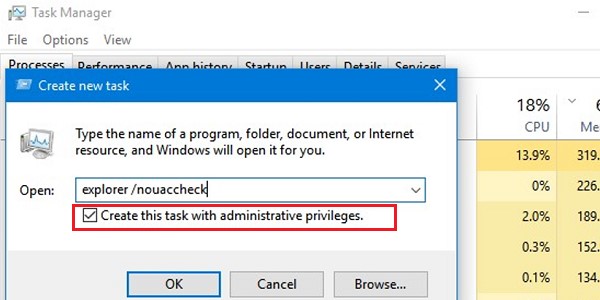
Or you can start a new privileged explorer process from Task Manager -> File -> Run New Task -> explorer.exe /nouaccheck (be sure to check the option “Create this task with administrative privileges”).
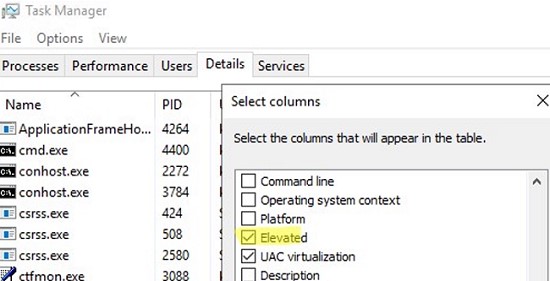
You can make sure that Windows Explorer is now running elevated in the Task Manager. Open the Task Manager and go to the Details tab. Right-click any column, click Select columns and enable Elevated column to be displayed.
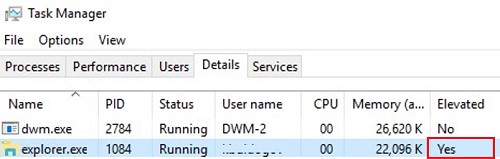
As you can see, explorer.exe is now having attribute Elevated=Yes.
After that Explorer will be able to open any system folder without a UAC warning, and all child processes run from Windows Explorer will run elevated.
If you often need to run explorer.exe in the elevated mode, you can create a *.bat or *.ps1 file with above commands on your desktop.
When you’re done, be sure to restart the explorer.exe in non-elevated mode:
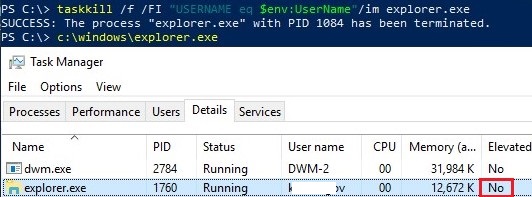
taskkill /f /FI "USERNAME eq $env:UserName"/im explorer.exe
explorer.exe
As you can see, now the Elevated value for the explorer.exe process has changed to No.
This Windows Explorer elevation trick works on both Windows Server 2016/2019 and all Windows 10 builds.
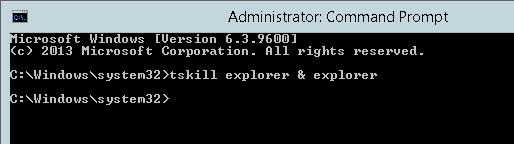
On Windows Server 2012/R2 and Windows 8, in order to run the Explorer process elevated, you need to open cmd.exe as administrator and run the command:
tskill explorer & explorer
11 comments
I tried this from a Windows 10 LTSB 2015 machine and it didn’t work. I was excited to see the article because you are correct this is a pain. Do you have any suggestions?
This trick only works on Windovs Server 2012 R2
Ok, that makes sense then. Thanks.
Not working on Windows Server 2016. Always starts explorer.exe without Elevated privileges
Try this – start an elevated command prompt, open task manager, right-click explorer.exe in details pane, and ‘End task’. Then, switch to the command prompt and run explorer. Seems to prevent the auto-restart of explorer.exe when you try it the above way.
What you need to do on W10/WS2016 and newer is:
– open Task Manager
– kill Explorer.exe process
– click the File menu, select Start new task, type: explorer /nouaccheck, be sure to tick the ‘Create this task with administrative privileges’
– click OK, there’s your elevated Explorer again
worked beautifully thanks brskie
Reading the title i thought it would be a way, as being a simple user, launching explorer as an administrator…
So i tried the trick New-ItemProperty -Path “HKCU:\Software\Policies\Microsoft\Windows\CurrentVersion\Explorer” -Name ShowRunasDifferentuserinStart -Value 1 -PropertyType DWORD -Force but Explorer key doesn’t exist (win10 20H2) and i don’t have right to create it, and, after the modification of GPEDIT.msc, as the explorer is not available in the start menu to run it as another user this is not possible either (knowing that it would have to be able to mix the two techniques when you have to close the explore … so no solution)
This trick assumes that you are logon Windows with an account that is a member of the local Administrators group.
ExplorerShellUnelevated
\CreateExplorerShellUnelevatedTask
S-1-5-18
false
false
false
IgnoreNew
6
true
PT10M
PT1H
true
false
true
C:\Windows\explorer.exe
/NOUACCHECK (NO|UAC|CHECK)
These commands will terminate the explorer.exe process for
the current user and start a new one, which will inherit
the elevated access token that powershell.exe is run with.
CreateExplorerShellUnelevatedTask is a system task created by Windows to prevent users and apps from running Windows Explorer process elevated