Let’s see how to track who reset the password of the particular user account in Active Directory using domain controllers security logs.
You can track password reset events using audit policies. First of all, you need to enable the audit account management policies in your AD domain. To do it:
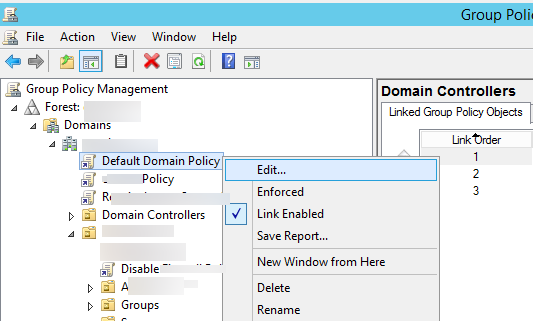
- Open Group Policy Management (gpmc.msc) console and edit Default Domain Policy.
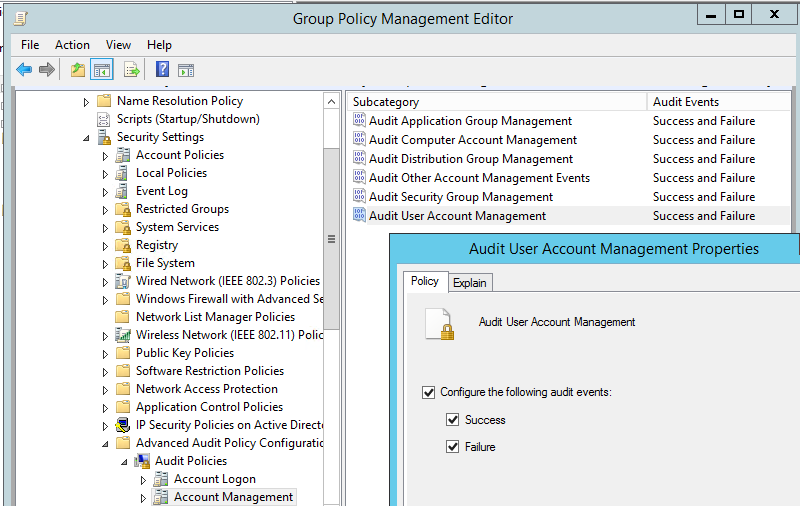
- Then in the Group Policy Editor, go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy.
- Find Audit User Account Management policy and enable it (if you want to log both successful and failed attempts of changing passwords, select Success and Failure).Note. You can enable this policy in the Advanced Audit Policy section as well (Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration).
- After applying the GPO on the clients, you can try to change the password of any AD user.
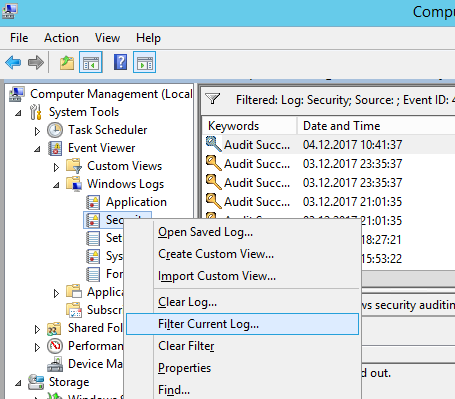
- Then open the Event Viewer on your domain controller and go to Event Viewer -> Windows Logs -> Security. Right-click the log and select Filter Current Log.
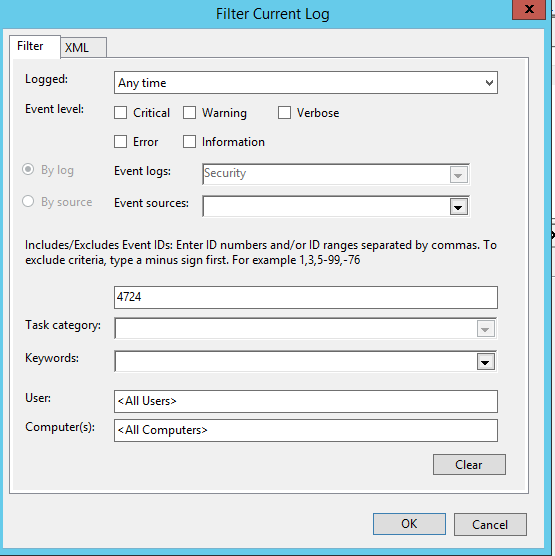
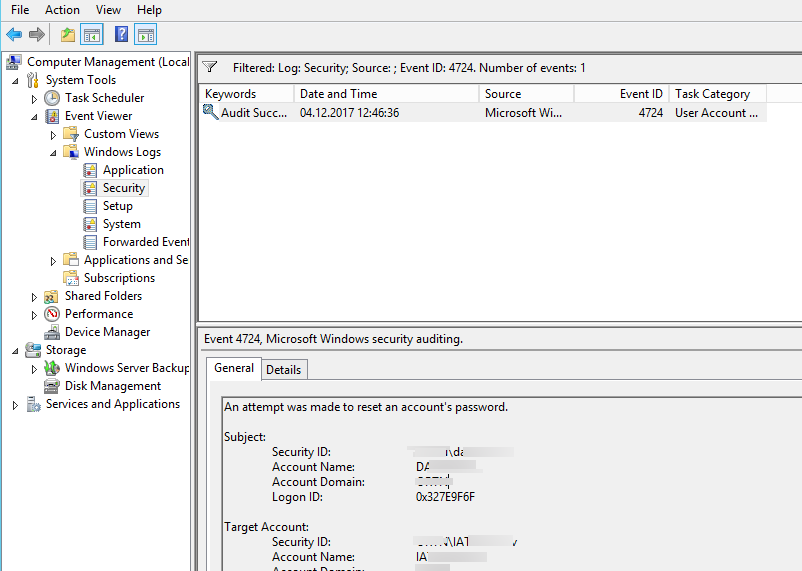
- In the filter parameters, specify that you only need to display events with the EventID 4724.
- Only the events of successful password change will be left in the list. (An attempt was made to reset an account’s password.) In the information about the event you can see the administrator account who has changed the password (Subject:) and the name of the user account whose password has been reset (Target Account:).
- 4724 (628 in previous Windows Server versions) – An attempt was made to reset an account’s password (administrator reset user password)
- 4723 (627 in previous Windows Server versions) – An attempt was made to change an account’s password (the user changed the password himself)
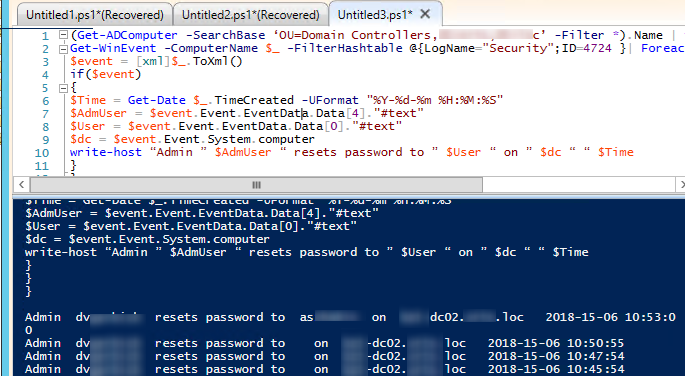
You can get the information about this events from all Active Directory domain controllers using Get-ADComputer and Get-WinEvent PowerShell cmdlets:
(Get-ADComputer -SearchBase ‘OU=Domain Controllers,DC=woshub,DC=com’ -Filter *).Name | foreach {
Get-WinEvent -ComputerName $_ -FilterHashtable @{LogName="Security";ID=4724 }| Foreach {
$event = [xml]$_.ToXml()
if($event)
{
$Time = Get-Date $_.TimeCreated -UFormat "%Y-%d-%m %H:%M:%S"
$AdmUser = $event.Event.EventData.Data[4]."#text"
$User = $event.Event.EventData.Data[0]."#text"
$dc = $event.Event.System.computer
write-host “Admin ” $AdmUser “ resets password to ” $User “ on ” $dc “ “ $Time
}
}
}
If necessary, you can save this info directly from PowerShell to an external MySQL database using MySQL .NET Connector according to the similar script described in the article How to detect who deleted a file from Windows shared folder.
3 comments
Hello,
You have a great, but why edit the Default Domain Policy and not Default Domain Controllers Policy ?
Best Regards
Hi
Am really impressed by this PS script that will fetch the “User’s ( single user) Password History ” however am not sure where in below script we have to specify the user name,
Can any one help me on the same and if you already used this please post the place where i can input the user name
for which we get history of the password reset…You can get the information about this events from all Active Directory domain controllers using Get-ADComputer and Get-WinEvent PowerShell cmdlets:
(Get-ADComputer -SearchBase ‘OU=Domain Controllers,DC=woshub,DC=com’ -Filter *).Name | foreach {
Get-WinEvent -ComputerName $_ -FilterHashtable @{LogName=”Security”;ID=4724 }| Foreach {
$event = [xml]$_.ToXml()
if($event)
{
$Time = Get-Date $_.TimeCreated -UFormat “%Y-%d-%m %H:%M:%S”
$AdmUser = $event.Event.EventData.Data[4].”#text”
$User = $event.Event.EventData.Data[0].”#text”
$dc = $event.Event.System.computer
write-host “Admin ” $AdmUser “ resets password to ” $User “ on ” $dc “ “ $Time
}
}
}
You can try to replace the folowing code line in the above PowerShell script:
write-host “Admin ” $AdmUser “ resets password to ” $User “ on ” $dc “ “ $Time
to
if ($user -eq “a_smith” – {write-host “Admin ” $AdmUser “ resets password to ” $User “ on ” $dc “ “ $Time}
a_smith – is the username for wich you want to get the password reset history in AD.