You can use Remote Desktop Shadowing to remotely connect to user sessions on Windows computers. This feature is essentially an analog of Remote Assistance and allows administrators to remotely view and interact with the user’s desktop both on desktop versions (Windows 11 or 10) and on Windows Server RDS servers.
Enable Remote Desktop Shadow Connection Mode in Windows
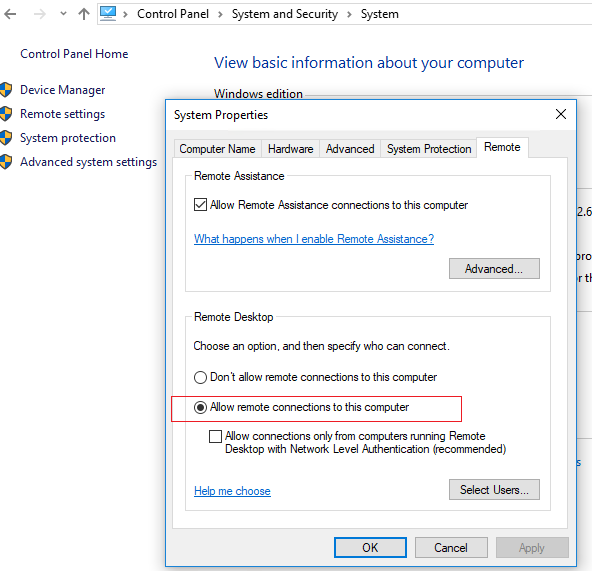
You need to configure the Windows computers you want to connect to via the remote desktop shadow connection in a certain way.
- Enable Remote Desktop (RDP) on user computers (manually or via GPO);
- Your account must have local administrator permissions on the user’s computer (you can add the user to the ‘Administrators’ group manually or using Group Policies);
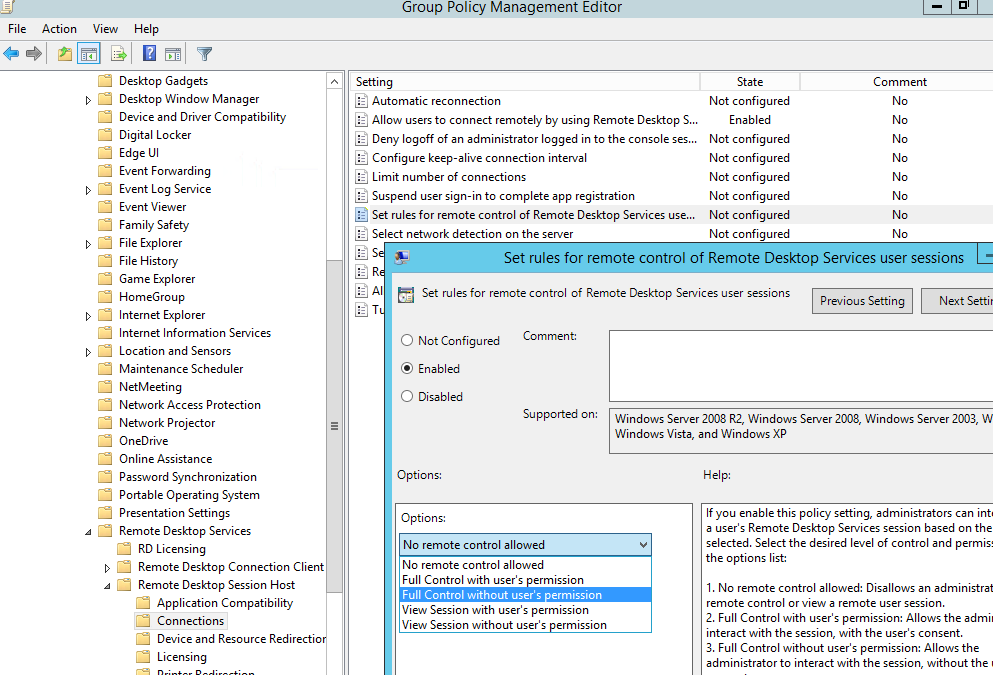
- Configure the shadow connection mode. You can configure whether you need to request the user confirmation to connect and whether view or control is allowed in the shadow session. You can configure shadow connection mode through the GPO option Set rules for remote control of Remote Desktop Services user sessions (Computer Configuration -> Administrative Templates -> Windows components -> Remote Desktop Services -> Remote Session Host -> Connections).
The following 5 modes are available:0 – disable shadow remote control;
1 — full control with user’s permission;
2 — full control without user’s permission;
3 — view session with user’s permission;
4 — view session without user’s permission - You can enable the desired shadow connection mode directly through the registry. Edit the registry manually or with the reg add command. In this example, we set mode 4, which allows the remote session to be viewed without the user’s permission:
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v Shadow /t REG_DWORD /d 4By default, this registry parameter is not set and the shadow connection is performed in full control mode with user confirmation. - Configure Windows Defender Firewall rules to allow incoming remote shadow connections. The following ports are used for session shadowing traffic in Windows, instead of the standard 3389/RDP port: 139/TCP, 445/TCP, and a range of dynamic RPC ports (from 49152 to 65535). To allow incoming shadow connection traffic, you must enable two pre-defined firewall rules in Windows:
File and Printer Sharing (SMB-In)andRemote Desktop - Shadow (TCP-In). The last rule allows remote access to theRdpSa.exeprocess. You can enable Windows Defender rules on user computers through a GPO or by using the Enable-NetFirewallRule PowerShell cmdlet.
Remotely Connect to a User Session via Remote Desktop Shadowing
Let’s look at how to remotely connect to another user’s desktop session on a remote Windows computer using the Remote Desktop shadow connection. In this example, I will connect from my Windows 11 computer to the user’s session on the user’s Windows 10 workstation.
The built-in Remote Desktop Connection tool (mstsc.exe) is used to shadow connect to the user’s session. The command format is:
Mstsc.exe /shadow:<Session ID> /v:<Computer name or IP address>
You can also use one of the following mstsc options:
- /prompt – request a user credential to connect (if not specified, you will be connected with the current user credentials);
- /control – the mode that allows interacting with the user session. If the parameter is not set, you will be connected to a user session in a view mode, i. e. you won’t be able to control a user’s mouse or enter data from the keyboard;
- /noConsentPrompt – don’t prompt the user for confirmation to connect to a desktop session.
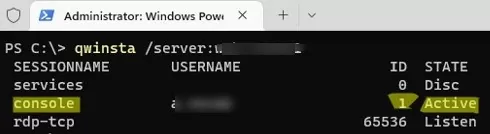
Now you need to find out the username and his session ID on the remote computer (if the user works directly at the computer console, then his session ID will always be 1).
Let’s display a list of user sessions on a remote computer (it can be a desktop computer running Windows 11/10 or Windows Server with the Remote Desktop Services Host role).
Let’s remotely request the list of sessions on Windows 10 workstation using this command:
qwinsta /server:PC_Name01
In this example, you can see that there is only one user logged into the computer, who works directly at the computer console (SESSIONNAME=console) with session ID=1.
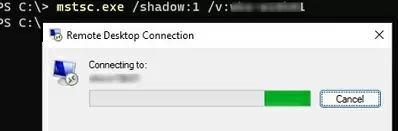
Let’s try remotely connecting to this user’s desktop via a shadow connection. Run the command:
Mstsc /shadow:1 /v:PC_Name01
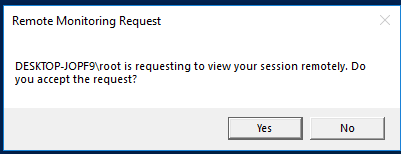
The Windows user will be prompted to confirm that an administrator is connecting to their session:
Remote connection request PC\admin is requesting to view your session remotely. Do you accept the request?
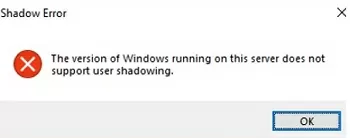
The version of Windows running on this server does not support user shadowing.
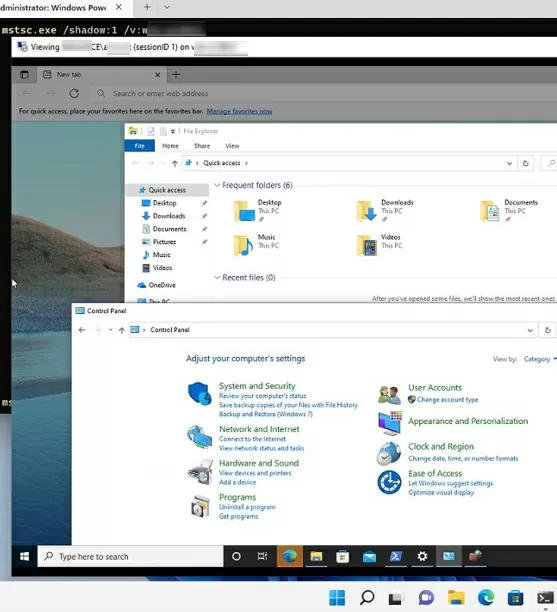
If the user accepts the connection, you’ll connect to his console session and see the user’s desktop. You will see all user actions, but won’t be able to control (interact) this session. If you want to control his session, use the /control option in the mstsc command. In this case, the caption in the window title will change from Viewing username (sessionID 1) on computername to Controlling…
If a user session is locked because the user is inactive or a UAC privilege escalation request appears when connecting without using the mstsc /control parameter, the shadow session window becomes black and a pause symbol appears on it.
The shadow session goes into a suspended state if the user has a UAC prompt on the Secure desktop. After the user confirms the UAC action, your shadow session will resume.
- Use the keyboard shortcut
Ctrl + Alt + Breakto resize the shadow connection window to fit the entire screen of your desktop; - Press
Alt+*on the computer (orCtrl+*on the RDS server) to end the shadow session.
You can notify a user that someone is remotely connecting to their session via an RDP shadow connection by using the following PowerShell script:
while($true){
if (Get-Process -Name "RdpSa" -ErrorAction SilentlyContinue){[console]::beep(1000,500);Write-Host "RdpSa is running at $(Get-Date)"}
Start-Sleep -Seconds 1
}
You can run this PowerShell script as a Windows service. In this example, we’re notifying the user with a simple beep. Also, you can show a pop-up notification on the desktop.
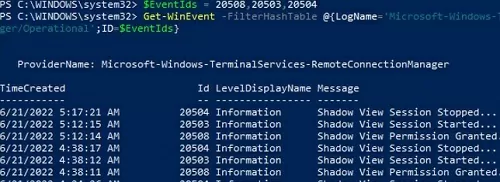
You can query a shadow connections history on a user computer from the Windows event logs. ll events of interest to you can be found in the Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational section of the Event Viewer.
- Event ID 20508 — Shadow View Permission Granted
- Event ID 20503 — Shadow View Session Started
- Event ID 20504 — Shadow View Session Stopped
You can get shadow connection logs from a user’s computer using PowerShell:
$EventIds = 20508,20503,20504
Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational';ID=$EventIds}
Remote Desktop Shadowing is available in Windows 11/10/ 8.1 and Windows Server 2022/2019/2016/2012 R2. Thus, you can use the Remote Desktop Shadowing as an analog of Remote Assistance or TeamViewer/AnyDesk, which provide instant and secure access to users’ computers on a local corporate network.
 The following 5 modes are available:0 – disable shadow remote control;
The following 5 modes are available:0 – disable shadow remote control;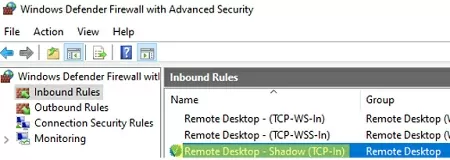
23 comments
Is there a possibility to list the shadow sessions that are running in a host? If yes, how to kick / close them?
Hi 🙂
Can this also work over the internet?
Yes, the RD session shadowing will work if your Windows 10 computer is assigned a public IP address and the connection to it is not blocked by firewalls.
Thanks 🙂
Hello, I assigned a public IP address but the connection is error, I watch wireshark traffic log the handshake IP is private IP, how can I use RDP shadowing with Public IP, thanks.
Hello,
When running : qwinsta /server:
I keep getting “ERROR 1722 RPC server is unavailable
I made sure all of the following services are running an automatic:
DCOM Server Process Launcher
RPC Endpoint Mapper
RPC
RPC Locator
Also made sure Firewall is allowing Remote Assistance
Checked Network Setting to ensure Printer & File sharing is allowed & IPV6 is enabled
Also ensured the following is enabled :
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server
I’m using Windows 10 to try to shadow a VM on my network.
I also updated the settings on the host on which the VM was created/lives to the same as above.
Would appreciate your help. Thank you.
is the username set up on both machines in parallel?
Thanks! Works like a charm except there’s one little problem – RPC random port. So this works only if the firewall is disabled OR a specific port open, but I can’t seem to be able to define a port on connection. Whenever I try for example “Mstsc.exe /control /shadow:1 /v:remotepcname:56772” I get a Shadow Error “This computer name is invalid.” Any advice?
You are right. In order for the RDP Shadow function to work properly, you need to open the entire range of RPC ports (49152 to 65535) on your firewall.
I don’t know a way to fix the RPC port number for shadow connections.
probably related: https://support.microsoft.com/en-us/help/2897666/this-computer-name-is-invalid-error-message-when-you-try-to-shadow-a-r
Any way of getting this working without the prompt on target machine?
Hello, how can you check if someone might be viewing your desktop via remote shadowing?
I recently setup a Win10 Pro system for my son’s virtual classes. With kids being kids, I would like to monitor his screen activity from time to time just to make sure he’s not on another screen while his class is going on.
I’ve been reading a couple threads but still can’t get RDP shadowing to work.
mstsc /v: works.
mstsc /v: /shadow:1 /noconsentprompt /control returns “This computer name is invalid.”
His system is new so qwinsta returns his ID as 1. Definitely no issue with the command syntax.
I’ve opened firewall ports 443,49152-65535 on both our systems but still no go. Is there any detailed walkthrough on how to setup RDP shadowing for home network or this is only doable in server OS?
hi do you have any solution? I am also having the same issue
Better to raise your kid to make good decisions and live by the consequences of bad ones, rather than spy on them.
But he should definitely be monitoring how the teacher is running the classroom, and what curriculum is being presented.
To anyone having a connection problem or error messages upon a shadow connection attempt, here’s how I fixed it.
On the client computer:
1 – Open PC Settings > Network > Sharing Options
2 – Expand the profile that says “(current profile)” and click “Turn on file and printer sharing” and click “Save changes”
3 – Open PC Settings > System > Remote Desktop > Disable, then Enable
4 – Go to Start and type “services.msc” (without the quotes) and press enter
5 – Find “Remote Desktop Services” > right-click it > Restart > Yes
Afterwards, try to connect. You can make these changes through the registry remotely, but you’d have to restart for the changes to take effect.
The fact that after all these yyears this shit still doesnt work right or they change it and I can’t connect via LAN to another PC in my home and/or shadow it without more than 5 minutes of setup is rediculous.
Windows 21H2, Windows compilation 19044.1766
termsrv.dll 10.0.19041.1741
Add line in Patches.txt for TermsrvPatcher https://github.com/geissbuehler/TermsrvPatcher
x64, 39 81 3C 06 00 00 0F 84 73 55 01 00, B8 00 01 00 00 89 81 38 06 00 00 90
Is there a way to view another user’s session on the same PC? e.g. a user’s machine set up with separate accounts – one for work use and one for personal use – it would be great to be able to view the personal a/c without having to switch user accounts all the time
Desktop versions of Windows only support one concurrent RDP session. So, when you switch between your accounts, your second second session is frozen.
All of a sudden, on my Windows 2019 RD servers I can’t Shadow users sessions. I can send the request, they get it and click OK to give me control and nothing launches on my end from the CB server. Was working fine for 2 years till a few weeks ago 🙁
Check for the latest installed updates. One of them could break some shadow connection functionality.